This page has been urgently created to contain information regarding WannaCrypt, or better known as the WannaCry encryption ransomware virus.
While the full extent of the damages caused so far remains unclear, the latest estimates place it at over 200k victims in over 150 countries.
The main difference to other ransomware malware, WannaCry infects via a recently disclosed vulnerability in the Windows operating system and does not rely on the user opening a ‘bad’ email.
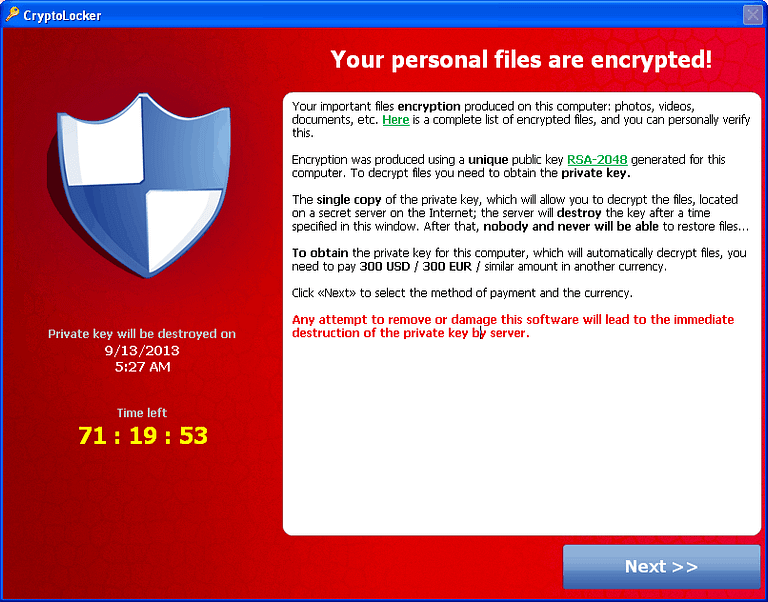
Why Is It Dangerous?
The hackers take advantage of a Microsoft Windows exploit developed by the NSA, nicknamed EternalBlue, which was reportedly leaked and dumped by the Shadow Brokers hacker group last month.
The exploit can infect computer systems running un-patched versions of Windows by taking advantage of flaws in Microsoft Windows’ SMB (Server Message Block).
Once a single computer in an organisation or home is hit by WannaCry, the worm looks for other vulnerable computers within the local network to infect.
How Can It Be Prevented?
Microsoft released a patch, called MS17-010, for the vulnerability back in March 2017. Those who have not patched their computer systems should do so immediately and do a virus and malware cleanup.
How to check if you have the Microsoft patch that closes the vulnerability in Windows?
Download this script we created and decompress it to create the Wannacry folder. Run the runme.cmd to run the PowerShell script to detect for the relevant Microsoft security patches. It will let you know if you have the one of the patches installed.
Microsoft KB Updates Checked
Related Links
Microsoft Official MS17-010 Technet: MS17-010 Technet Patch Document
For older systems, such as Windows XP and Windows Server 2003, you can find the Microsoft patches on this page: https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
WannaCry Live Map: WannaCrypt Live Global Infection Map

