CryptoLocker or Trojan:Win32 / Crilock.A
Cryptolocker encrypted trojan really does encrypt work data and personal files and is incredibly damaging, resulting in requiring urgent virus cleanup of computers and across the local network. This trojan is very unlike most other ransomware viruses in that this one really does damage files.
It can traverse across network resources (servers, NAS, mapped network shares) and encrypt anything with write access. The infection is not dependent on being a local administrator. Most security programs, at the time of writing this article, do not identify the infection until the damage is done.
The countdown timer is real and your opportunity to pay them does go away when it lapses. There is a version that demands $100 and a newer version that demands $300. No other variants reported at the time of this writing.
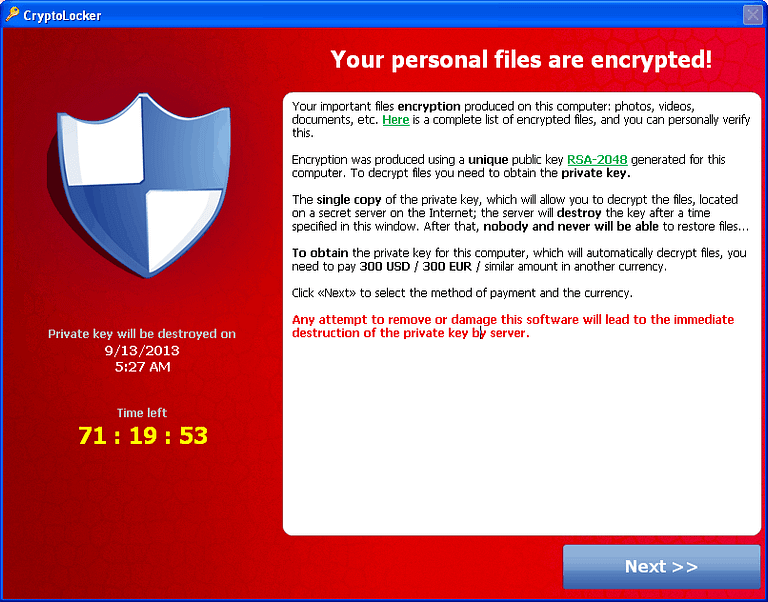
CryptoLocker message states the following:
‘Your personal files are encrypted!
Your important files encryption produces on this computer: photos, videos, documents, etc. Here is a complete list of encrypted files, and you can personally verify this.
Encryption was produced using a unique public key RSA-2048 generated for this computer. To decrypt files, you need to obtain the private key.
The single copy of the private key, which will allow you to decrypt the files, located on a secret server on the Internet; the server will destroy the key after a time specified in this window. After that, nobody and never will be able to restore files…
To obtain the private key for this computer, which will automatically decrypt files, you need to pay 100 USB / 100EUR / similar amount in another currency.
Click Next to select the method of payment and the currency.
Any attempt to remove or damage this software will lead to the immediate destruction of the private key by server.’
Attack Vectors
CryptoLocker has three infection vectors:
- This infection was originally spread via email with the infected attachment and sent to company email addresses that pretend to be customer support related issues from Fedex, UPS, DHS, etc. Emails can also appear as normal everyday emails and to come from internally using the same domain your business uses.
- Through exploit kits located on hacked web sites that exploit vulnerabilities on your computer to install the infection. This is commonly known as a drive by infection. The infected code is usually placed inside an advertisement banner on the targeted website.
- Through trojans that pretend to be programs required to view online videos. These are typically encountered through porn or pirated software sites.
Also, already infected machines of the Zeus botnet have had the virus pushed to them directly.
The File Encryption Method
Once the system has been successfully infected and a communication channel to the command and control server (C&C server) has been established, the malware will start the encryption process by requesting a randomised encryption key.
A typical request includes the version of the malware, a numeric id, the system’s network name, a group id as well as the language of the system. As soon as the infection specific RSA key has been obtained, the malware will look for files to encrypt. It does so by searching through all connected drives, including mapped network shares, for files matching one of the following patterns:
*.odt, *.ods, *.odp, *.odm, *.odc, *.odb, *.doc, *.docx, *.docm,
*.wps, *.xls, *.xlsx, *.xlsm, *.xlsb, *.xlk, *.ppt, *.pptx,
*.pptm, *.mdb, *.accdb, *.pst, *.pdf, *.dwg, *.dxf, *.dxg, *.wpd,
*.rtf, *.wb2, *.mdf, *.dbf, *.psd, *.pdd, *.eps, *.ai, *.indd,
*.cdr, ????????.jpg, ????????.jpe, img_*.jpg, *.dng, *.3fr,
*.arw, *.srf, *.sr2, *.bay, *.crw, *.cr2, *.dcr, *.kdc, *.erf,
*.mef, *.mrw, *.nef, *.nrw, *.orf, *.raf, *.raw, *.rwl, *.rw2,
*.r3d, *.ptx, *.pef, *.srw, *.x3f, *.der, *.cer, *.crt, *.pem,
*.pfx, *.p12, *.p7b, *.p7c
Cryptolocker uses a Domain Generation Algorithm to find command & control servers. It is not one particular server. It does indeed need to reach a live C&C before encrypting.
Decryption of Files
Once the encryption of the data is complete, decryption is not possible (update: see bottom of this article). Unfortunately, you are also not aware of the encryption process until it has completed and it alerts you.
To obtain the file specific AES key to decrypt a file, you need the private RSA key corresponding to the RSA public key generated for the victim’s system by the C&C server. The recommended solution is to restore encrypted files from a backup.
There has been reports paying the ransom has started the decryption process, if paid within the time limit. However, it takes a fairly long time for the payment to be received and the decryption to finish.
Other methods to get your files back is to recover any files that have been backed up by VSS, the Volume Shadow Copy Service. Essentially VSS allows recovery of ‘previous versions’ of the file and is truly an excellent component of the Windows operating system. However, these ransomware viruses typically wipe the VSS copies, but it is definitely worth trying recovery here.
Reinfected a previously cleaned machine will not allow you a solution either. The new installation will use a different key and thus cannot be used to decrypt previously encrypted files.
Recovering Data
Not much can be done in decrypting data that has already been encrypted, but there are tools that can be used to recover files from VSS (previous versions). Ensure this Windows component is turned on.
Other tools are;
ListCrilock.exe – generates a list of files that have been encrypted.
Shadow Explorer – will display any files/folders and recover via VSS
Encrypted files have ownership changed to the infected user. This is a good method of determining who has the infected computer in a large network/server infrastructure.
Important: If you are attempting to use Previous Versions (Shadow Copy) to restore files, ensure you copy the restored files to a different hard drive rather than restoring them on the same drive as the encrypted files. If the disk space on the drive gets low enough, Shadow Copy snapshots could be automatically deleted by the system due to a low disk space condition.
The oldest shadow copy of volume \?Volume{…} was deleted to keep disk space usage for shadow copies of volume \?Volume{…} below the user defined limit.
Prevention
On servers configured for a domain, group policies can be configured to block this from running in the first place and has a good chance at stopping the infection from getting to your network infrastructure like servers and workstations.
To do this we need to setup software restriction policies (SRPs) to disallow the executing of executable .exe files from the AppData and AppData/Roaming folders in the Windows user profiles.
Because Cryptolocker usually comes with another rootkit/trojan called ZBot we need to protect against this as well.
The following SRP path restrictions should be:
SRP Policy #1 – This is for Cryptolocker executables.
Path: %AppData%\*.exe
Security Level: Disallowed
Description: Don’t allow executables from AppData.
SRP Policy #2 – This is for ZBot executables.
Path: %AppData%\*\*.exe
Security Level: Disallowed
Description: Don’t allow one subfolder under AppData.
Note!: There may be collateral damage associated with these due to blocking legitimate programs, but definitely worth it. You will need to monitor and provide workarounds for these wanted programs.
For those trying to block execution using Software Restriction Policies, the following extra Path rules seems effective at preventing users from opening executable files directly from a .zip, .rar, .7z file (as apposed to extracting the file first then running the executable). The general behavior for email users is to open the attachment directly from within their email program.
SRP Policy #3 – Block executables run from archive attachments opened with WinRAR:
Path: %Temp%\Rar*\*.exe
Security Level: Disallowed
Description: Don’t allow executables opened within WinRar.
SRP Policy #4 – Block executables run from archive attachments opened with 7zip
Path: %Temp%\7z*\*.exe
Security Level: Disallowed
Description: Don’t allow executables opened within 7zip.
SRP Policy #5 – Block executables run from archive attachments opened with WinZip
Path: %Temp%\wz*\*.exe
Security Level: Disallowed
Description: Don’t allow executables opened within winzip.
SRP Policy #6 – This is for preventing executables in zip compressed attachments in email and explorer (ie malware payloads).
Path: %temp%\*.zip\*.exe
Security Level: Disallowed
Description: Prevent opening executables from .zip files (ie email attachments)
This should work on Windows 8 and Windows 7. This SRP rule will block when the zip file is opened from the email program (e.g Outlook), webmail (IE download) and directly in windows explorer. This rule may not work vs other third-party zip handlers or other operating systems such as Vista or WinXP.
UNC and Mapped Drives of Network Resources
Cryptolocker does not parse and encrypt network shares, only mapped drives – this is a very important consideration.
By changing all your computers to use UNC paths (ie \\computer\share) rather than a mapped drive of it (ie Z:) you will be preventing an avenue of encryption on your network resources. Another method is making mapped shares read-only will mitigate the risk of having sensitive data on the server encrypted – this will obviously impact productivity since you now cannot write to this share.
Highly recommended is keeping an up to date Internet Security package is paramount even if this infection does get through, as vendors will be updating to safe guard against it. To date a number of AV packages fails to stop this infection, but the detection rate amongst anti-virus programs is rapidly improving.
Total Virus report on a Cryptolocker sample: https://www.virustotal.com/en/file/b3530b7519660996d28eb31a8d5b585ec60601843c77dd9f2b712812c99843e4/analysis/
Backup! Backup! Backup!!
Make sure you have valid backups with redundancy and they are professionally checked! We are talking about backups that have snapshot history or backups that can be taken offline. Any automatic synchronisation software would be useless since the encrypted files would flow to the synchronised backup method. This is usually the only method to recover from this infection.
Update – 12 August 2014
There is now a hopeful method to decrypt your encypted files simply by going to this site and submitting a encrypted file; https://www.decryptcryptolocker.com/
For a professional malware cleanup with our experts or to discuss future preventative measures for your company or home network, or a cleanup and moving forward from this infection, please give us a call on 1300 466 766 or (02) 6628 7779 if you are in the Northern Rivers, NSW region.

